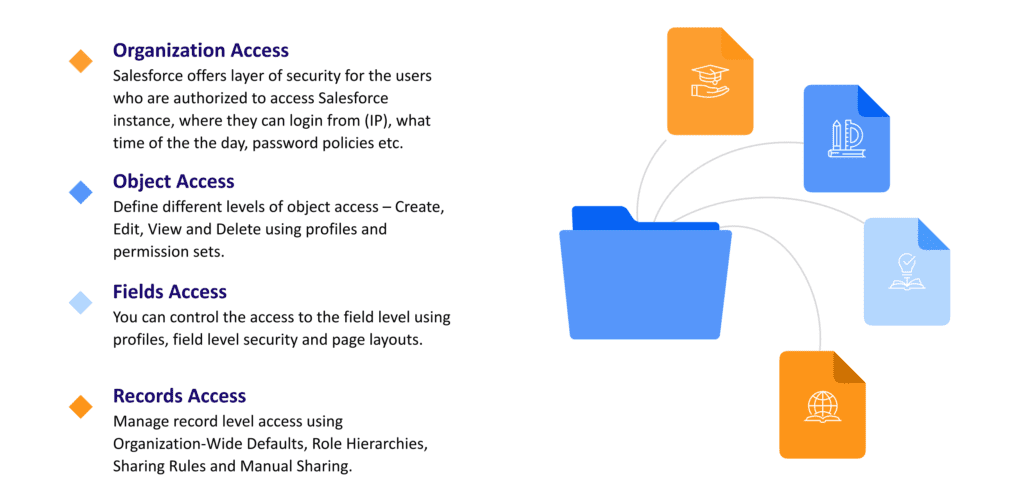
Salesforce Data Security Model. Salesforce is the world's #1 customer… | by Shreya Gaggad | Salesforce.com | Medium
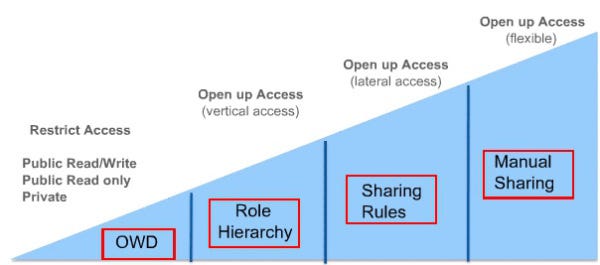
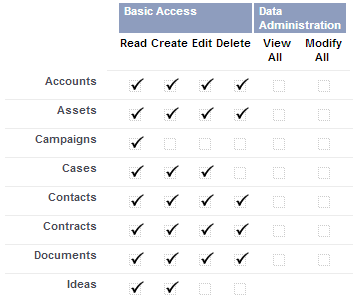
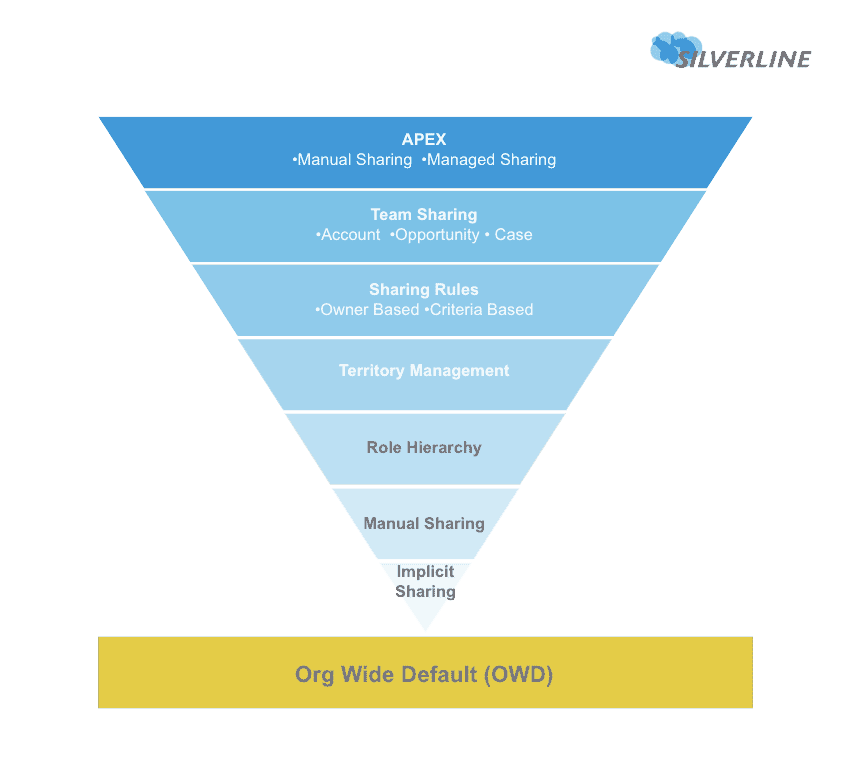
![The data access security model - Salesforce CRM - The Definitive Admin Handbook - Fourth Edition [Book] The data access security model - Salesforce CRM - The Definitive Admin Handbook - Fourth Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781786468963/files/graphics/image_04_001.jpg)
The data access security model - Salesforce CRM - The Definitive Admin Handbook - Fourth Edition [Book]

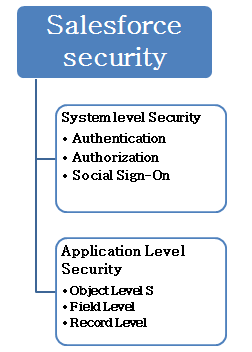
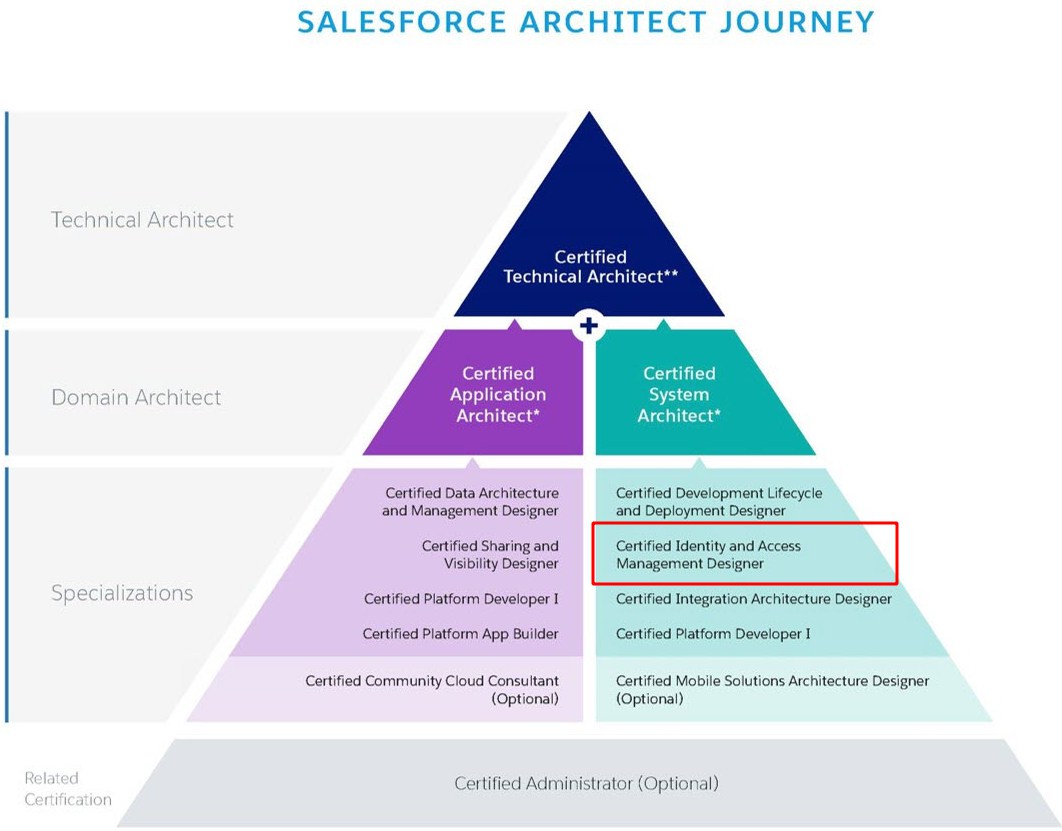
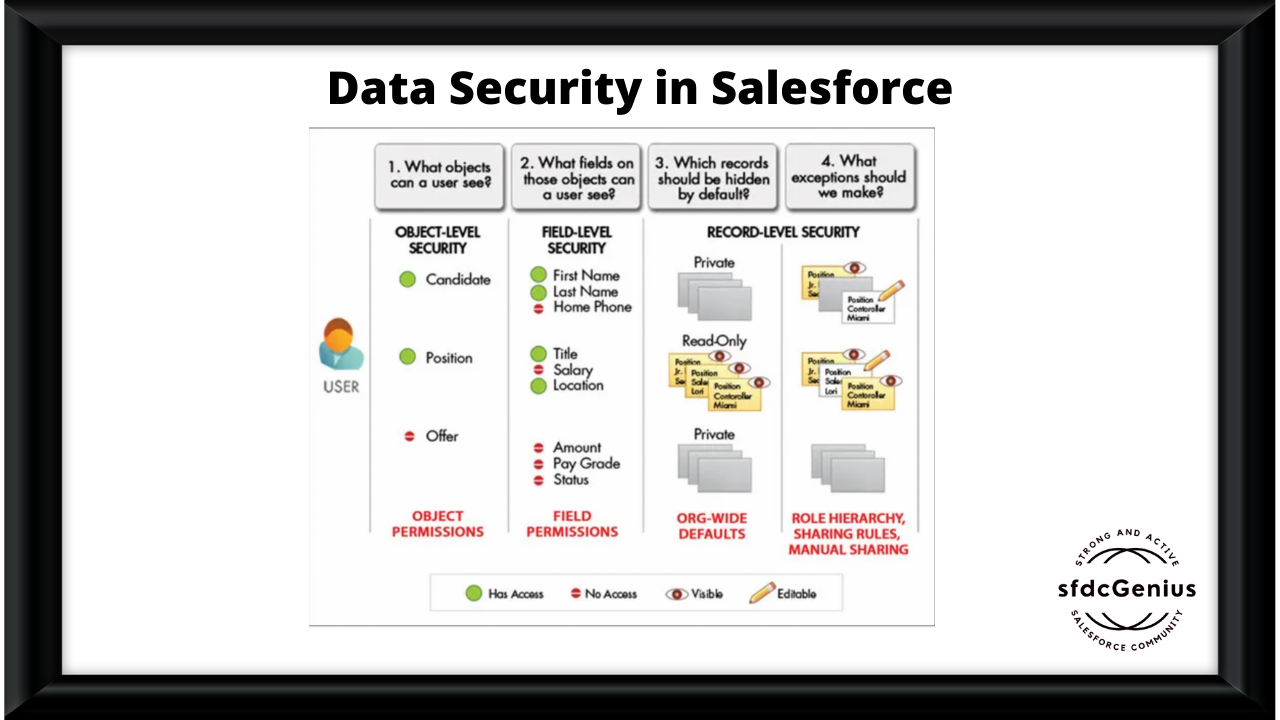
Salesforce Security Sharing Model or the layer of visibility | Salesforce, Salesforce developer, Salesforce administrator